| Home | Trees | Indices | Help |
|
|---|
|
|

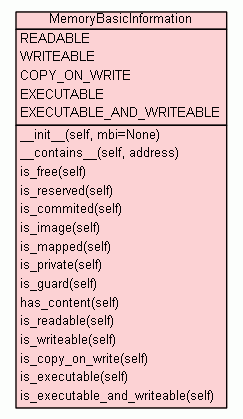
Memory information object returned by VirtualQueryEx.
|
|||
|
|||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
|
Inherited from |
|||
|
|||
READABLE = 238
|
|||
WRITEABLE = 204
|
|||
COPY_ON_WRITE = 136
|
|||
EXECUTABLE = 240
|
|||
EXECUTABLE_AND_WRITEABLE = 192
|
|||
|
|||
|
Inherited from |
|||
|
|||
x.__init__(...) initializes x; see help(type(x)) for signature
|
Test if the given memory address falls within this memory region.
|
|
|
|
|
|
|
|
|
|
|
Note: Tipically data sections in executable images are marked like this. |
Note: Executable pages are always readable. |
Note: The presence of such pages make memory corruption vulnerabilities much easier to exploit. |
| Home | Trees | Indices | Help |
|
|---|
| Generated by Epydoc 3.0.1 on Fri Dec 20 17:55:08 2013 | http://epydoc.sourceforge.net |