September 06, 2010
shabti_auth_repozepylons – auth’n’auth in Pylons using repoze.wh[o|at]¶
This template brings repoze.who’s authentication and repoze.what’s authorisation functions to Pylons, plus an identity model expressed in SQLAlchemy, making it immediately accessible to extension and development.
Warning
Documentation and template are incomplete as at September 06, 2010.
About repoze-pylons auth’n’auth¶
Gustavo Narea has done some sterling work in developing a number of repoze-based plugins to make life easier for web app developers, with the specific aim of making repoze configuration a more tractable task. He has recently released a repoze-pylons plugin, something that more or less amounts to a zero-config plugin for use specifically with Pylons (and/or TG).
Gustavo observes:
This plugin provides optional and handy utilities for Pylons applications using repoze.what.
Some of the features of the plugin include:
- The utilities are ready to use: There’s nothing additional to be configured before using.
- 100% documented. Each component is documented along with code samples.
- The test suite has a coverage of 100% and it will never decrease – if it ever does, report it as a bug! TurboGears 2 is officially supported as well.
The Shabti auth_repozepylons template uses Gustavo’s repoze-pylons plugin to provide a basic auth’n’auth setup following the scheme used in the other Shabti auth’n’auth templates. A basic identity model is set up and a couple of examples of repoze decorators are used to provide the authorisation checks.
The repoze.what plugin provides access control decorators and other utilities to support the development of authorisation schemes for web apps. Authentication (logging/signing in/out) functionality is provided by Chris McDonough’s repoze.who which runs as middleware. The overview show below is lifted straight from the repoze.who docs .
Note
Overview
repoze.who is an identification and authentication framework for arbitrary WSGI applications. It acts as WSGI middleware.
repoze.who is inspired by Zope 2’s Pluggable Authentication Service (PAS) (but repoze.who is not dependent on Zope in any way; it is useful for any WSGI application). It provides no facility for authorization (ensuring whether a user can or cannot perform the operation implied by the request). This is considered to be the domain of the WSGI application.
It attempts to reuse implementations from paste.auth for some of its functionality.
Note
shabti_auth_repozeplyons source code is in the bitbucket code repository
Using the template¶
After successfully installing Shabti, additional paster templates will be available. Simply create a Shabti-configured project by specifying that paster should use the shabti auth repozewho template:
$ paster create -t shabti_auth_repozepylons myproj
These are the option dialogue choices appropriate for the Shabti auth template — which uses mako templates and SQLAlchemy ...
(mako/genshi/jinja/etc: Template language) ['mako']:
(True/False: Include SQLAlchemy 0.4 configuration) [False]: True
(True/False: Setup default appropriate for Google App Engine) [False]:
Once the project has been created, navigate to the project directory and run the (brief) test suite:
$ nosetests
XXX tests should executed successfully. If the tests succeeded, the next step is to initialise the store by running the project setup script:
$ paster setup-app development.ini
If successful, the setup script will stream the log of database transactions to stdout, e.g.:
CREATE TABLE user_groups__group_users (
user_id INTEGER NOT NULL,
group_id INTEGER NOT NULL,
PRIMARY KEY (user_id, group_id),
CONSTRAINT user_groups_fk FOREIGN KEY(user_id)
REFERENCES user (id),
CONSTRAINT group_users_fk FOREIGN KEY(group_id)
REFERENCES "group" (id)
)
Once the database has been initialised, start the Pylons web app with:
$ paster serve --reload development.ini
The Shabti repozeplyons auth template’s variant on the standard Pylons welcome screen is browsable at at http://localhost:5000/ ...
Welcome screen¶
signin page¶
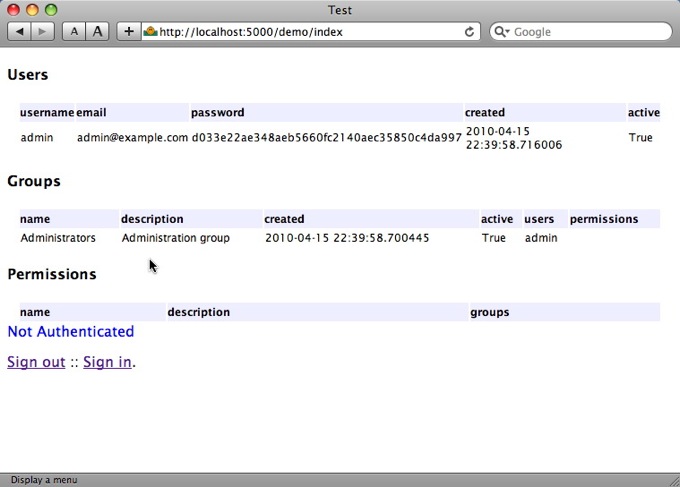
shabti model unauthenticated¶
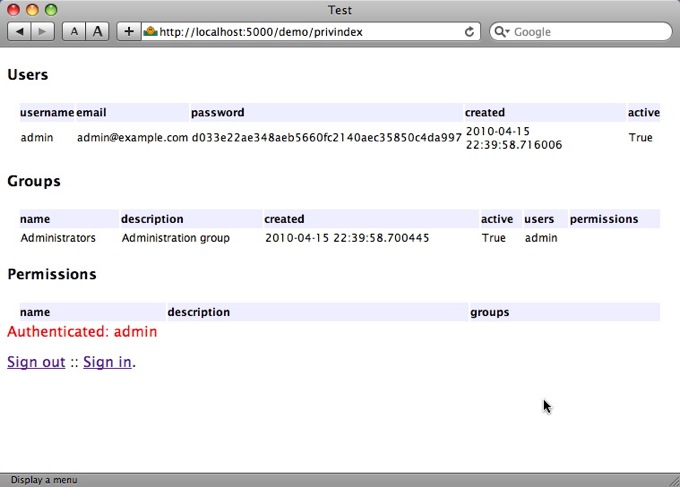
shabti model authenticated¶
Notes on the template¶
See also
More information generally about creating and using repoze-pylons predicates can be found in Protecting controllers and controller actions .
| author: | Graham Higgins <gjh@bel-epa.com> |
|---|
September 06, 2010